nginxとTomcatによる高速かつセキュアなWebシステムの構築
nginxとTomcatによる高速かつセキュアなWebシステムの構築を説明する。
目次
nginxとTomcatによる高速かつセキュアなWebシステムの構築
1.概要
nginxとTomcatを利用した高速かつセキュアなWebシステムの構築を行う。
nginxをリバースプロキシ、キャッシュサーバ、ロードバランサとして動作させ、HTTPS終端、アクセス制御などを行う。
注意:本手順はセキュリティレベルの厳密な検証は行っていない為、最新のセキュリティ設定を行う必要があります。
「ssl_ciphers」の値については専用サイト(※)の内容を確認し、最新版を適用する必要があります。
2.構成イメージ
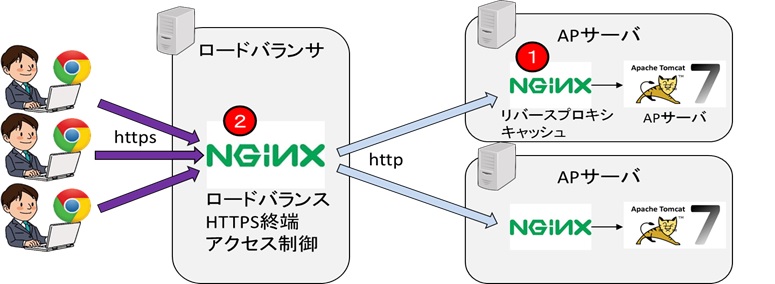
- リーバースプロキシとして動作させ、URI Rewriteやコンテンツキャッシュ処理を行う。
- L7ロードバランサとして動作させ、HTTPS終端やアクセス制御を行う。
3.リバースプロキシ(①)のnginxの構築
[nginxのソースビルドでのインストール]を参考にリーバスプロキシ2台を構築する。
各nginxはローカルのTomcat(http://127.0.0.1)に接続する。
./configure
make
make install
【nginx.conf】
#user nobody;
user nginx nginx; #Edited
worker_processes 1;
pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
tcp_nopush on;
keepalive_timeout 65;
gzip on;
gzip_min_length 30;
open_file_cache max=1000 inactive=120s;
server {
listen 80;
server_name Ruby;
location / {
proxy_buffering on;
proxy_buffer_size 8k;
proxy_buffers 64 8k;
proxy_pass http://127.0.0.1:8080;
}
#error_page 404 /404.html;
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
}4.ロードバランサ(②)の構築
nginxのインストール(HTTPS/HTTPS2を利用可能)
[root@Alabaster nginx-1.12.2]# ./configure --with-http_ssl_module --with-http_v2_module --with-http_realip_module
checking for OS
+ Linux 2.6.32-431.el6.x86_64 x86_64
checking for C compiler ... found
+ using GNU C compiler
+ gcc version: 4.4.7 20120313 (Red Hat 4.4.7-18) (GCC)
checking for gcc -pipe switch ... found
checking for -Wl,-E switch ... found
checking for gcc builtin atomic operations ... found
checking for C99 variadic macros ... found
checking for gcc variadic macros ... found
checking for gcc builtin 64 bit byteswap ... found
checking for unistd.h ... found
checking for inttypes.h ... found
checking for limits.h ... found
checking for sys/filio.h ... not found
checking for sys/param.h ... found
checking for sys/mount.h ... found
checking for sys/statvfs.h ... found
checking for crypt.h ... found
checking for Linux specific features
checking for epoll ... found
checking for EPOLLRDHUP ... found
checking for EPOLLEXCLUSIVE ... not found
checking for O_PATH ... not found
checking for sendfile() ... found
checking for sendfile64() ... found
checking for sys/prctl.h ... found
checking for prctl(PR_SET_DUMPABLE) ... found
checking for sched_setaffinity() ... found
checking for crypt_r() ... found
checking for sys/vfs.h ... found
checking for nobody group ... found
checking for poll() ... found
checking for /dev/poll ... not found
checking for kqueue ... not found
checking for crypt() ... not found
checking for crypt() in libcrypt ... found
checking for F_READAHEAD ... not found
checking for posix_fadvise() ... found
checking for O_DIRECT ... found
checking for F_NOCACHE ... not found
checking for directio() ... not found
checking for statfs() ... found
checking for statvfs() ... found
checking for dlopen() ... not found
checking for dlopen() in libdl ... found
checking for sched_yield() ... found
checking for SO_SETFIB ... not found
checking for SO_REUSEPORT ... found
checking for SO_ACCEPTFILTER ... not found
checking for SO_BINDANY ... not found
checking for IP_BIND_ADDRESS_NO_PORT ... not found
checking for IP_TRANSPARENT ... found
checking for IP_BINDANY ... not found
checking for IP_RECVDSTADDR ... not found
checking for IP_PKTINFO ... found
checking for IPV6_RECVPKTINFO ... found
checking for TCP_DEFER_ACCEPT ... found
checking for TCP_KEEPIDLE ... found
checking for TCP_FASTOPEN ... not found
checking for TCP_INFO ... found
checking for accept4() ... found
checking for eventfd() ... found
checking for int size ... 4 bytes
checking for long size ... 8 bytes
checking for long long size ... 8 bytes
checking for void * size ... 8 bytes
checking for uint32_t ... found
checking for uint64_t ... found
checking for sig_atomic_t ... found
checking for sig_atomic_t size ... 4 bytes
checking for socklen_t ... found
checking for in_addr_t ... found
checking for in_port_t ... found
checking for rlim_t ... found
checking for uintptr_t ... uintptr_t found
checking for system byte ordering ... little endian
checking for size_t size ... 8 bytes
checking for off_t size ... 8 bytes
checking for time_t size ... 8 bytes
checking for AF_INET6 ... found
checking for setproctitle() ... not found
checking for pread() ... found
checking for pwrite() ... found
checking for pwritev() ... found
checking for sys_nerr ... found
checking for localtime_r() ... found
checking for posix_memalign() ... found
checking for memalign() ... found
checking for mmap(MAP_ANON|MAP_SHARED) ... found
checking for mmap("/dev/zero", MAP_SHARED) ... found
checking for System V shared memory ... found
checking for POSIX semaphores ... not found
checking for POSIX semaphores in libpthread ... found
checking for struct msghdr.msg_control ... found
checking for ioctl(FIONBIO) ... found
checking for struct tm.tm_gmtoff ... found
checking for struct dirent.d_namlen ... not found
checking for struct dirent.d_type ... found
checking for sysconf(_SC_NPROCESSORS_ONLN) ... found
checking for openat(), fstatat() ... found
checking for getaddrinfo() ... found
checking for PCRE library ... found
checking for PCRE JIT support ... not found
checking for OpenSSL library ... found
checking for zlib library ... found
creating objs/Makefile
Configuration summary
+ using system PCRE library
+ using system OpenSSL library
+ using system zlib library
nginx path prefix: "/usr/local/nginx"
nginx binary file: "/usr/local/nginx/sbin/nginx"
nginx modules path: "/usr/local/nginx/modules"
nginx configuration prefix: "/usr/local/nginx/conf"
nginx configuration file: "/usr/local/nginx/conf/nginx.conf"
nginx pid file: "/usr/local/nginx/logs/nginx.pid"
nginx error log file: "/usr/local/nginx/logs/error.log"
nginx http access log file: "/usr/local/nginx/logs/access.log"
nginx http client request body temporary files: "client_body_temp"
nginx http proxy temporary files: "proxy_temp"
nginx http fastcgi temporary files: "fastcgi_temp"
nginx http uwsgi temporary files: "uwsgi_temp"
nginx http scgi temporary files: "scgi_temp"
[root@Alabaster nginx-1.12.2]# make;make install
make -f objs/Makefile
make[1]: ディレクトリ `/root/nginx-1.12.2' に入ります
cc -c -pipe -O -W -Wall -Wpointer-arith -Wno-unused-parameter -Werror -g -I src/core -I src/event -I src/event/modules -I src/os/unix -I objs \
-o objs/src/core/nginx.o \
src/core/nginx.c
cc -c -pipe -O -W -Wall -Wpointer-arith -Wno-unused-parameter -Werror -g -I src/core -I src/event -I src/event/modules -I src/os/unix -I objs \
-o objs/src/core/ngx_log.o \
src/core/ngx_log.c
・
・
・
・
test -d '/usr/local/nginx/logs' \
|| mkdir -p '/usr/local/nginx/logs'
test -d '/usr/local/nginx/logs' \
|| mkdir -p '/usr/local/nginx/logs'
test -d '/usr/local/nginx/html' \
|| cp -R html '/usr/local/nginx'
test -d '/usr/local/nginx/logs' \
|| mkdir -p '/usr/local/nginx/logs'
make[1]: ディレクトリ `/root/nginx-1.12.2' から出ます
[root@Alabaster nginx-1.12.2]#サーバー証明書作成のための鍵作成@HTTPサーバ
[root@Alabaster certs]# openssl genrsa -aes256 -out /etc/pki/tls/private/privkey.pem 2048
Generating RSA private key, 2048 bit long modulus
.......+++
.................................................................+++
e is 65537 (0x10001)
Enter pass phrase for /etc/pki/tls/private/privkey.pem:(パスワード)
Verifying - Enter pass phrase for /etc/pki/tls/private/privkey.pem:(パスワード)Webサーバ利用のパスワード無し鍵の作成@HTTPサーバ
[root@Alabaster certs]# openssl rsa -in /etc/pki/tls/private/privkey.pem -out /etc/pki/tls/private/privkey-nopass.pem
Enter pass phrase for /etc/pki/tls/private/privkey.pem:(パスワード)
writing RSA key発行要求CSRファイル作成@HTTPサーバ
[root@Alabaster certs]# openssl req -new -key /etc/pki/tls/private/privkey.pem -out /etc/pki/tls/certs/Alabaster.csr
Enter pass phrase for /etc/pki/tls/private/privkey.pem:(パスワード)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:JP
State or Province Name (full name) []:Tokyo
Locality Name (eg, city) [Default City]:Shinjuku
Organization Name (eg, company) [Default Company Ltd]:A-frontier co.,Ltd
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:Alabaster ←Webサーバのホスト名
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:(空)
An optional company name []:(空)サーバ証明書発行@認証局
[root@Cancer ~]# openssl ca -in /etc/pki/tls/certs/Alabaster.csr -out /etc/pki/tls/certs/Alabaster.crt.pem -days 3651 ←Alabaster.csr:HTTPサーバで作成した「発行要求CSRファイル」 Alabaster.crt.pem:サーバ証明書
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 0 (0x0)
Validity
Not Before: Oct 22 07:41:15 2017 GMT
Not After : Oct 21 07:41:15 2027 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = A-frontier co.,Ltd
commonName = Alabaster
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0C:0A:76:1B:99:C8:02:96:6D:67:F8:C4:62:73:9B:10:91:A4:98:0C
X509v3 Authority Key Identifier:
DirName:/C=JP/ST=Tokyo/L=Shinjuku/O=A-frontier co.,Ltd/CN=A-frontierCA
serial:BB:A2:16:04:96:D6:43:70
Certificate is to be certified until Oct 21 07:41:15 2027 GMT (3651 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updatedサーバ証明書の配置とnginxのSSL設定
[root@Alabaster ~]# ls -l /usr/local/nginx/ssl/
合計 16
-rw------- 1 root root 4623 10月 22 16:43 2017 Alabaster.crt.pem
-rw------- 1 root root 1679 10月 22 16:43 2017 privkey-nopass.pemnginxの設定:TLSの有効化
[root@Alabaster ~]# cat /usr/local/nginx/conf/nginx.conf
user nginx;
worker_processes 2;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
gzip on;
gzip_min_length 30;
# HTTPS server
server {
listen 443 ssl http2;
server_name Alabaster;
ssl on;
ssl_certificate /usr/local/nginx/ssl/Alabaster.crt.pem;
ssl_certificate_key /usr/local/nginx/ssl/privkey-nopass.pem;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
#ssl_ciphers HIGH:!aNULL:!MD5;
#ssl_prefer_server_ciphers on;
#location / {
# root html;
# index index.html index.htm;
#}
}
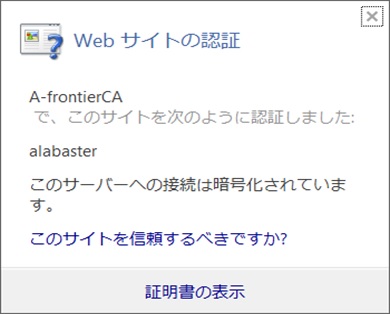
}サーバ名でアクセス(鍵マークが出ている)
負荷分散(L7)ロードバランサの設定
[root@Alabaster conf]# cat /usr/local/nginx/conf/nginx.conf
user nginx;
worker_processes 2;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
gzip on;
gzip_min_length 30;
upstream backends{
server 192.168.3.50:80 weight=1; #リバースプロキシ(①)のアドレス
server 192.168.3.53:80 weight=1; #リバースプロキシ(①)のアドレス
}
# HTTPS server
server {
listen 443 ssl http2;
server_name Alabaster;
ssl on;
ssl_certificate /usr/local/nginx/ssl/Alabaster.crt.pem;
ssl_certificate_key /usr/local/nginx/ssl/privkey-nopass.pem;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
#ssl_ciphers HIGH:!aNULL:!MD5;
#ssl_prefer_server_ciphers on;
location / {
proxy_pass http://backends; #全アクセスを[backends]に流す
}
}
}nginxを再起動
[root@Alabaster conf]# /etc/rc.d/init.d/nginx stop;/etc/rc.d/init.d/nginx start
nginx を停止中: [ OK ]
nginx を起動中: [ OK ]ロードバランサへアクセス ※2つのリバースプロキシ(①)に順番にアクセスしている